Check for anomalous operating system activities
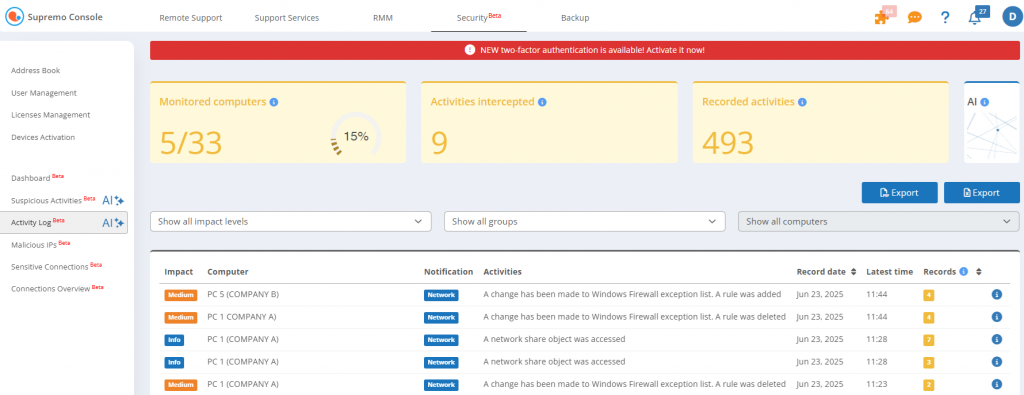
In the Activity Log, you can view a list of operating system activities identified as anomalous or suspicious on monitored devices, accompanied by their impact level: medium, high or critical.
Unlike other solutions on the market, IT Security does not show all operating system activities, which are often numerous and complex to analyse, but only those that are truly relevant and may represent signs of potential threats.
Activity analysis is based on the artificial intelligence of IT Security, which differs from traditional static approaches (often based on pre-trained models) thanks to a constantly evolving neural network.
This technology allows the system to dynamically adapt to the business environment, modelling its detection capabilities based on the actual behaviour of users and devices. The result is an increasingly accurate and personalised analysis of anomalies and threats.
During the first 14 days of using the add-on, the AI observes and learns the device’s habits, building a behavioural profile. It then continues to evolve, recognising any changes and reporting only truly suspicious activity to provide reliable, accurate and tailored protection.
For each activity recorded, the following information is reported:
- the level of impact
- the computer involved
- the notification
- the date of recording
- the time of the last occurrence
- the total number of detections
You can find detailed information by clicking on the recorded activity.
Data retention is 1 week.
Finally, you can perform custom searches and extract data in .csv and .pdf formats.

 Français
Français
 Deutsch
Deutsch
 Italiano
Italiano
 Português
Português
 Español
Español