Monitor devices, detect threats, avoid critical issues
IT Security is an advanced anomaly analysis system based on artificial intelligence, which integrates antivirus with behavioural detection and network monitoring functions, without the need for a SOC.
Unlike traditional AI models, it uses a continuously learning neural network, dynamically adapting to the business environment to constantly improve threat and anomaly detection.
The main strengths are:
- Advanced anomaly detection: identifies threats that escape traditional antivirus and XDR solutions.
- Continuous learning: adapts to evolving user and system behaviour.
- Accessibility: represents advanced security technology at an affordable price.
- RMM integration and remote control: simplifies the work of MSPs and MSSPs.
- Easy to activate, no complex configurations.
Offers holistic protection with multi-source analysis:
-
User and Machine Behaviour Monitoring: detects abnormal access, errors and suspicious changes.
- Detects suspicious user and device behaviour
- Analyses logins, user errors, and permission changes
- Identifies post-exploit activities and abnormal access attempts
-
Network monitoring:
- Analyses network traffic to identify suspicious scans
- Monitors shared folders and TCP/UDP connections
- Detects network scanning and intrusion activities
-
Cyber Intelligence:
- Identifies malicious DNS and IP addresses
- Provides indicators of compromise based on international threat intelligence
- Classifies malicious sites by privacy, social engineering and phishing.
IT Security features an intuitive and practical Dashboard, essential for real-time monitoring of your company’s IT infrastructure.
The Dashboard allows you to detect suspicious behaviour, identify threats and take prompt action to prevent critical issues.
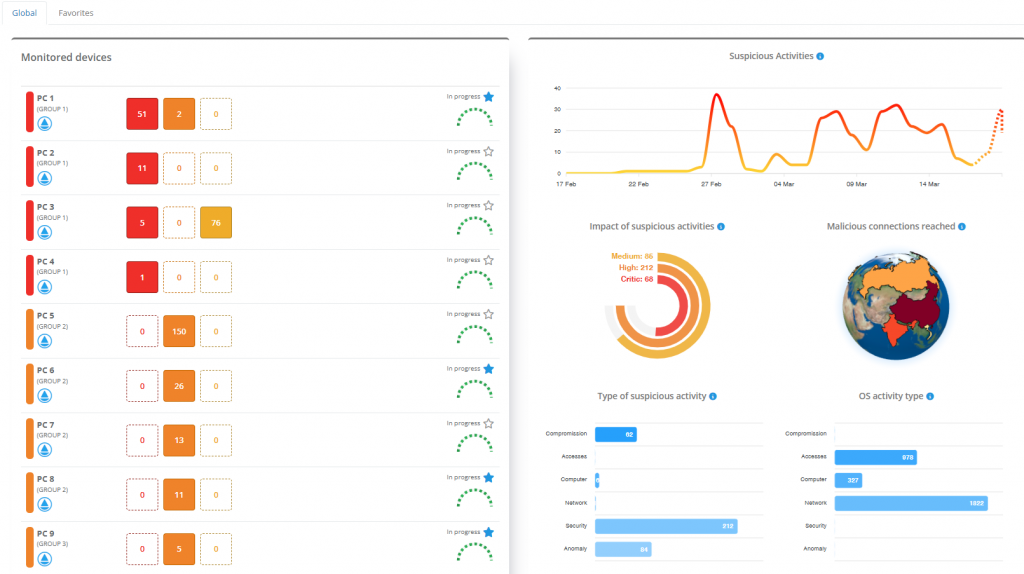
In the Monitored Devices section, you can:
- View devices with active Security features.
- Identify activities classified by impact level: high, critical or medium.
- Check the connection status of endpoints to the Management Console.
For efficient management, you can:
- Start remote connections via Supremo by clicking on the dedicated icon.
- Set up to 10 endpoints as favourites for quick and priority access to all detailed information.
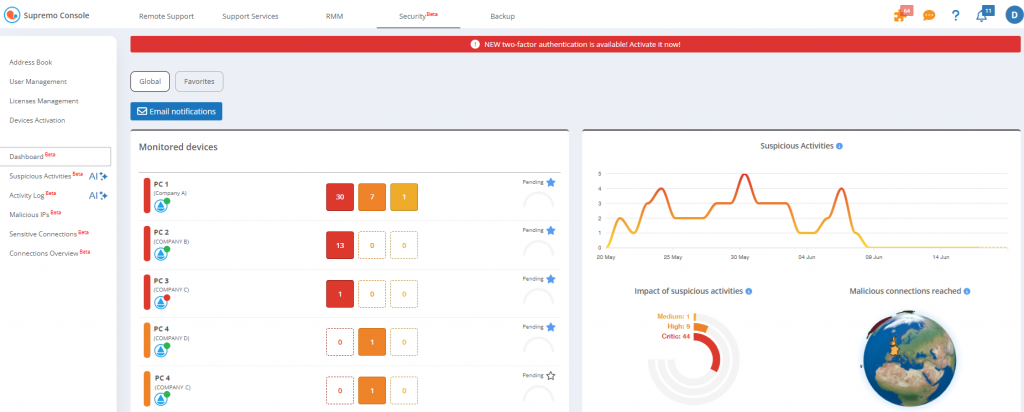
For devices marked as Favorites, you can access details of all activities that have occurred and notifications relating to the individual machine.
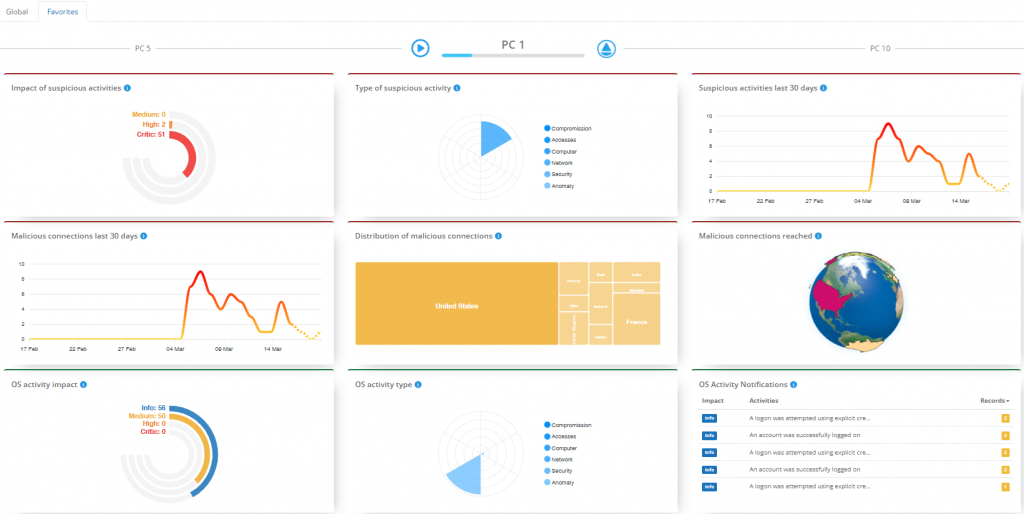
A scrolling view of your favourite endpoints is also available, which is ideal for monitoring on dedicated screens in operating environments.
You can stop scrolling to freeze a specific computer on the screen or start a remote connection with Supremo if you need to intervene on the machine.
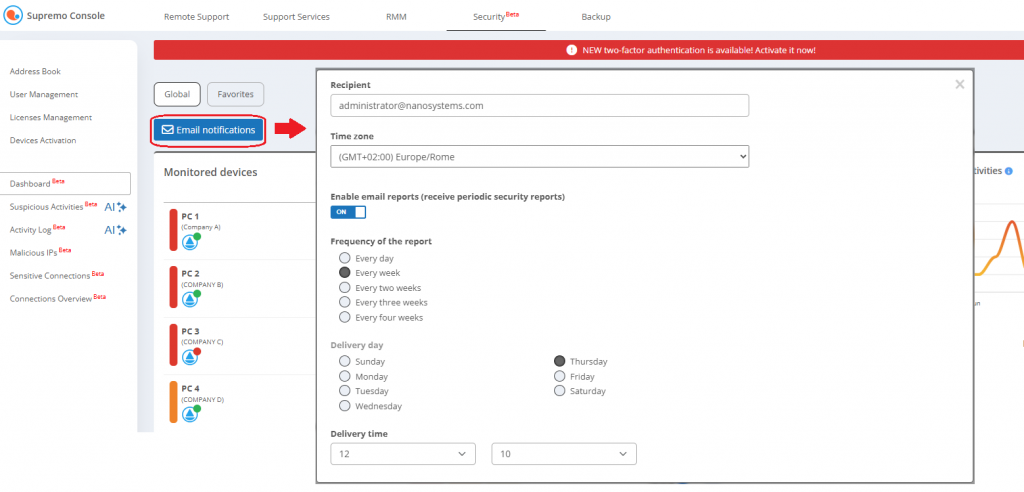
From the Dashboard, you can activate the periodic sending via email of a useful summary report of all monitored PCs, customising the recipient and the frequency of sending.
IT Security features are available on Windows systems starting from Windows 8.1 (Windows Server 2012 R2).

 Français
Français
 Deutsch
Deutsch
 Italiano
Italiano
 Português
Português
 Español
Español